Session Management Write-up - TryHackMe
Local Storage manipulation to escalate privileges
This room is about session management and how to exploit it.
We are given a website and we have to find some info about the website.
Escalating Privileges
First, I registered on the website as a student
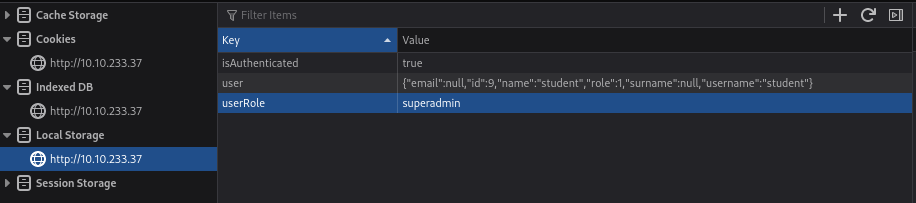
When I inspected local storage, I saw that there existed a userRole key with the value of student. At the same time, I noticed that there are three different roles: student, lecturer, and superadmin — from the requests sent to the server.
So, I changed the value of userRole to superadmin and refreshed the page.
I leveled up to superadmin role.
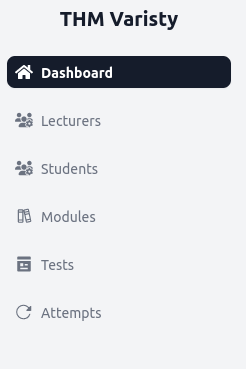
We have access to the admin panel now.
Questions
Now that we have access to the admin panel, we can answer the questions.
Question 1
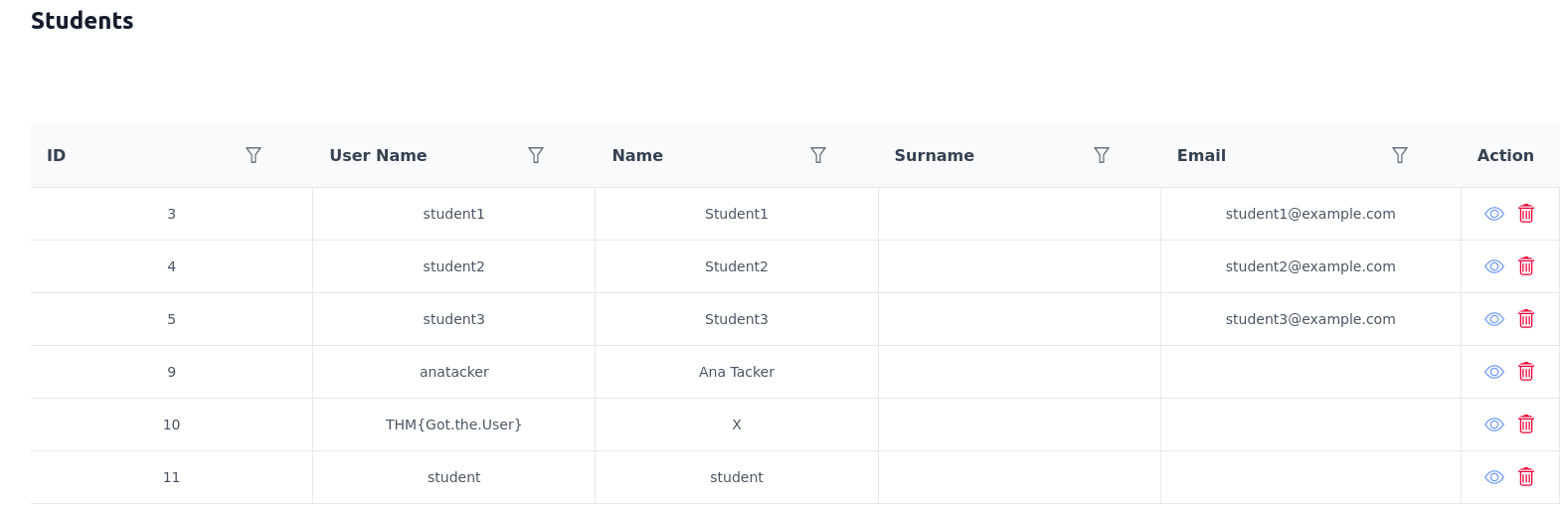
What is the username of the student with the name X?
From the students section, we can see the students’ information.
Answer: THM{Got.the.User}
Question 2
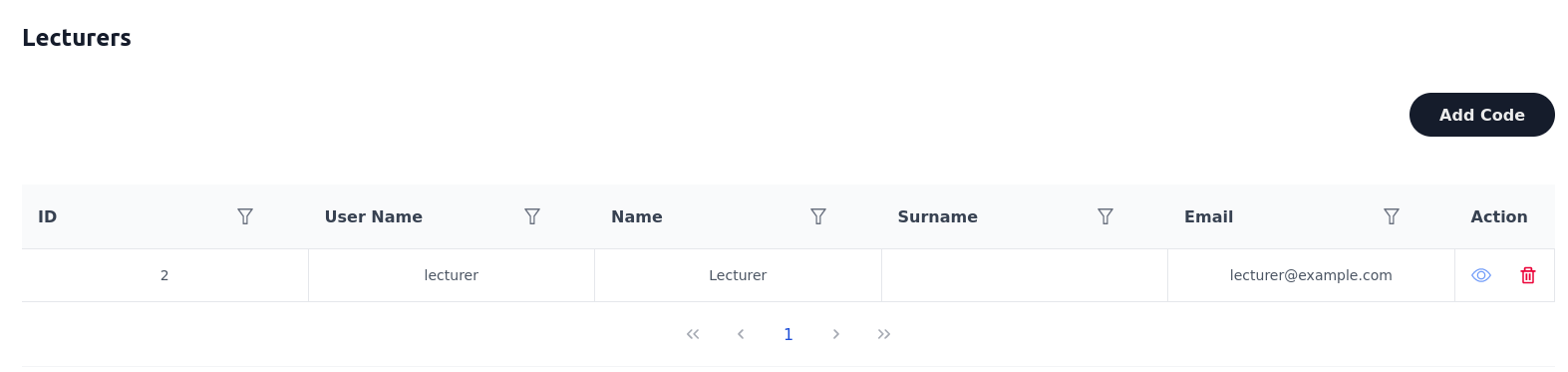
How many lecturers are registered on the application?
There is only one lecturer.
Answer: 1
Question 3
Excluding the unauthenticated user, how many roles does the application have?
There are three roles as we saw before: student, lecturer, and superadmin.
Answer: 3
Question 4
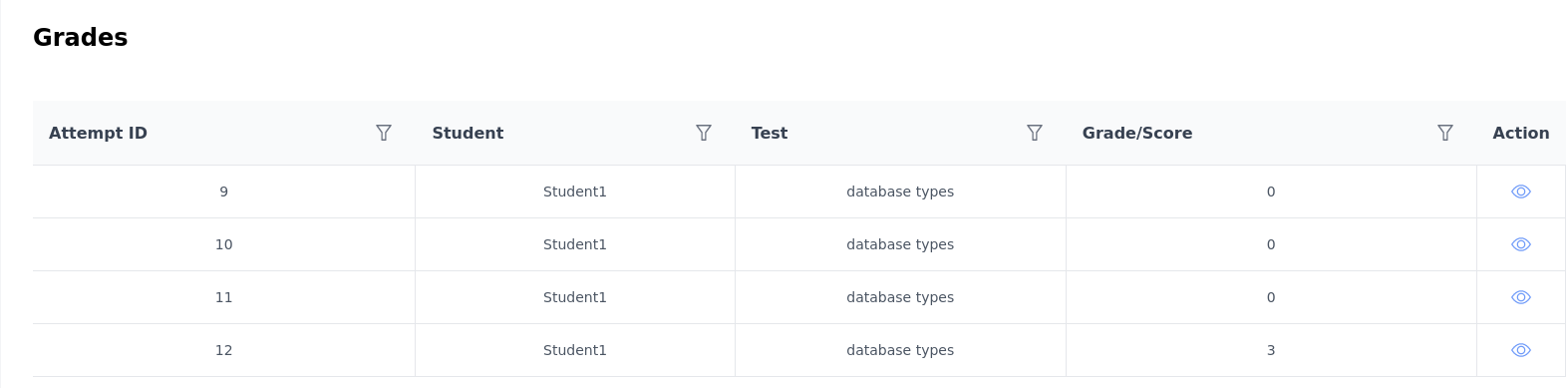
How many test attempts in total have been performed on the application?
On the grades section, we can see the test attempts.
Answer: 4
Question 5
What is the highest score that student1 has achieved on a test?
We can see the highest score from the previous screenshot.
Answer: 3
Question 6
What is the sequence of correct answers for the Database Types test? (Format y=yes and n=no, separated by commas)
On the Database Types Module, we can see the questions and answers.
Answer: y,n,n